Datalink Layer: Hop-to-Hop Communication and Frame Management
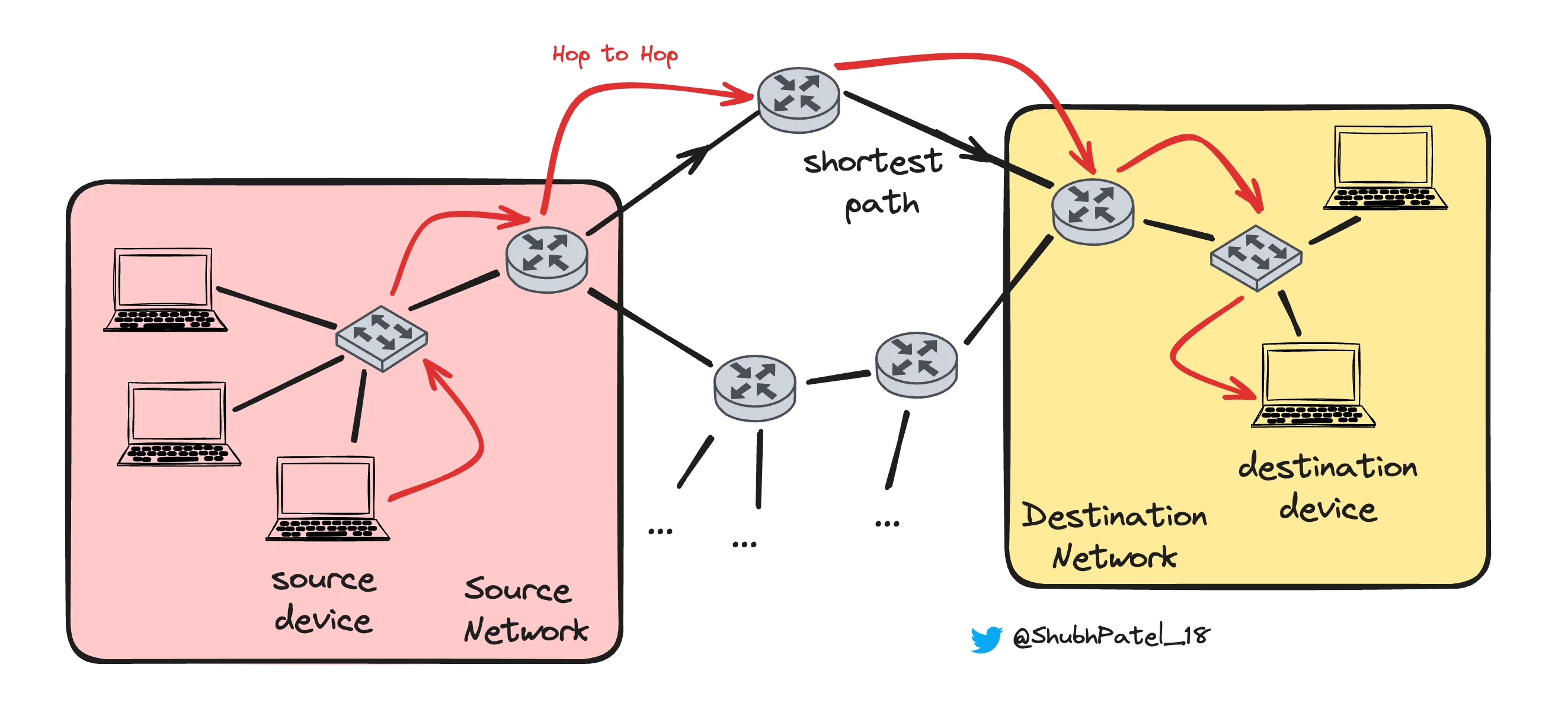
Diagram Illustrating Datalink Layer Operations
The Datalink Layer is an essential component of the OSI model, responsible for ensuring reliable communication between two directly connected devices in a network. It acts as a bridge, transforming packets received from the Network Layer into frames, which can then be transmitted over physical media.
Hop-to-Hop Delivery
Hop-to-hop communication refers to the process of transferring data between two devices that are directly connected, such as a computer to a router or between two routers. Unlike end-to-end delivery, which spans multiple devices across a network, hop-to-hop delivery focuses on ensuring data is accurately passed from one node to the next. This process uses MAC (Media Access Control) addresses to identify the source and destination devices within the same network segment.
Understanding Frames
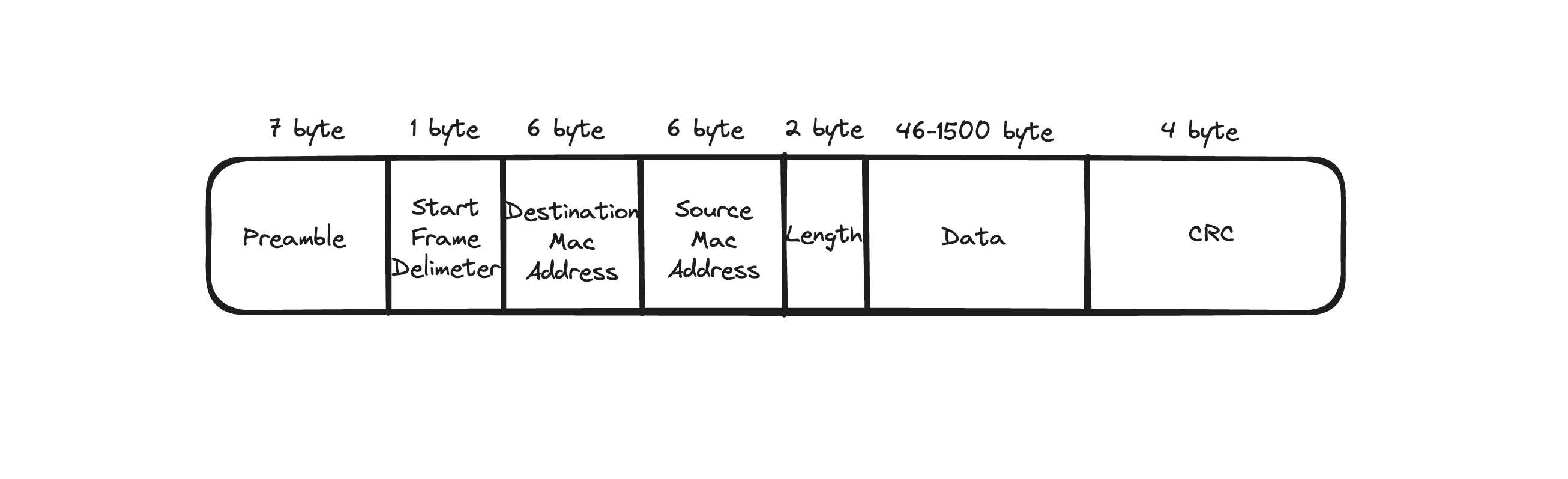
Structure of an IEEE 802.3 Ethernet Frame
Frames are the encapsulated data units in the Datalink Layer. A frame consists of a header, payload (data), and trailer, each serving a specific purpose:
-
Header: Contains control information, such as the source and destination MAC addresses.
-
Payload: The actual data being transferred.
-
Trailer: Includes error-checking information like CRC (Cyclic Redundancy Check) to ensure data integrity.
In Ethernet networks, a typical frame format might include:
-
Preamble: A sequence of bits to synchronize communication.
-
Destination MAC Address: Identifies the receiver's MAC address.
-
Source MAC Address: Identifies the sender's MAC address.
-
Type/Length: Indicates the protocol type (e.g., IPv4) or the payload length.
-
Payload: The data itself.
-
CRC: Used to detect errors in the transmitted frame.
Flow Control: Managing Data Transfer
While flow control is also addressed at the Transport Layer, the Datalink Layer implements flow control mechanisms on a per-link basis. This granularity helps prevent buffer overflow at intermediate devices (like routers) which may not have the same processing capability as the sending and receiving endpoints.
Scenario: Consider a situation where your device sends data to a router. The router might have a smaller buffer size compared to your device. Flow control ensures that your device does not overwhelm the router by sending data too quickly.
Error Control: Ensuring Data Integrity
The Datalink Layer also plays a crucial role in error detection and correction. Unlike the Transport Layer, which manages end-to-end error control, the Datalink Layer focuses on detecting errors that occur over a single link.
Cyclic Redundancy Check (CRC): This error-checking method involves generating a CRC value before transmission. The receiver recalculates the CRC using the same algorithm and compares it with the received value. If there is a mismatch, it indicates that errors occurred during transmission.
Access Control: Managing Shared Media
Access control at the Datalink Layer determines how multiple devices share and access the network medium, ensuring that collisions are avoided and all devices have fair access.
Wired Networks: Using CSMA/CD
In wired Ethernet networks, collisions can occur when multiple devices try to send data simultaneously. The Carrier Sense Multiple Access with Collision Detection (CSMA/CD) protocol helps manage this:
-
Listening: A device listens to the network to ensure no other devices are transmitting.
-
Collision Detection: If two devices transmit simultaneously, a collision is detected. Both devices stop, wait for a random period, and then retry.
-
Random Backoff: The random wait time minimizes the chance of repeated collisions.
Wireless Networks: Using RTS/CTS
In wireless networks, devices use additional mechanisms to avoid collisions:
-
RTS (Request to Send): A device sends an RTS signal to the Access Point (AP) indicating its intent to transmit.
-
CTS (Clear to Send): The AP responds with a CTS signal if the channel is idle, granting permission to transmit.
-
Acknowledgment (ACK): After the transmission, the AP sends an ACK to confirm successful data reception.
These protocols help manage traffic in wireless networks, reducing the likelihood of collisions and ensuring efficient data transmission.